Before we talk about the Case Study, let’s understand what Phishing is.
What is Phishing. How does this work when it actually works?
Phishing is a type of cybercrime where the attacker tricks you into entering your sensitive account information using a fake login page as the bait. Here, you are the fish, and that fake login page is the bait.
When you input your account details, and click Submit on this page, instead of going to the actual service provider’s server, the entered information goes to the attacker’s server. Some of the most common targets are – account number, username, password, email IDs, governament IDs, among others.
An important part of a phishing attack is the urgency factor. With the fake page URL, the attacker sends a message asking you to enter your information urgently, or you’ll lose something.
A few examples are:
- Your account may get blocked
- Your service may expire
- Your courier delivery may not be delivered
- You may get a fine
- You may miss a great discount/deal on a product/service
So, I received an SMS from an unknown number today. The message contents are:
Dear customer your sbi YONO account will be suspended by today please update your pan card now visit the link https://s44-fhvb.web.app
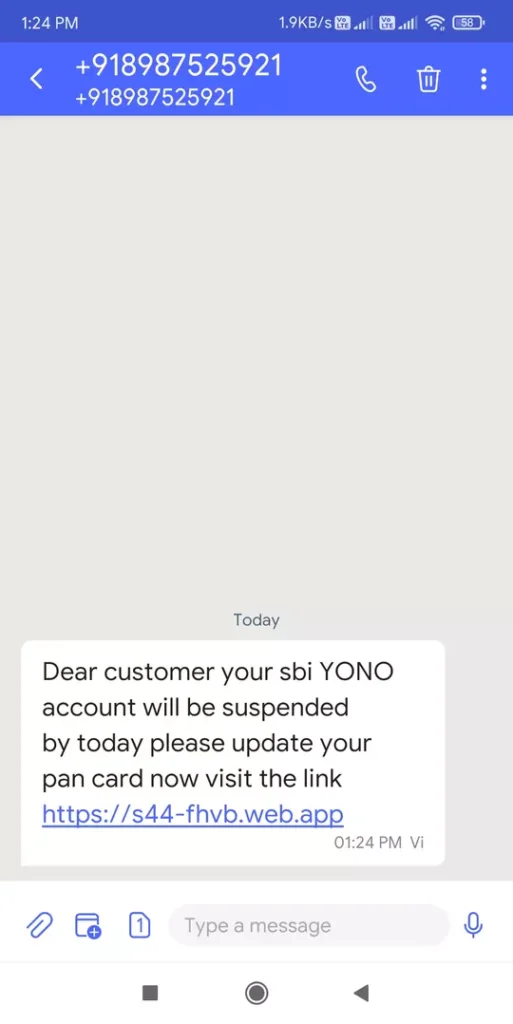
The phone number is +918987525921. Truecaller shows the location of the number to be Bihar, India.
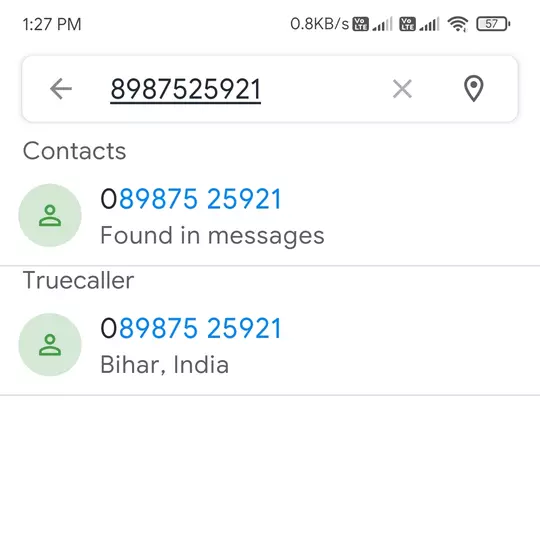
I received it on a number that’s actually registered with SBI.
So, the question is that has there been a data breach at the SBI, if yes, at what level:
- International-level since SBI has branches outside of India, too,
- National-level, only the Indian customers are affected, or
- Branch-level, only the customers of the branch I have account at are affected.
Or, the phishing message was sent to a random mobile number list.
Case Study: How does this Phishing attack work.
The attack URL is: https://s44-fhvb.web.app
It’s using on a free subdomain on the developer web.app domain, which redirects to Google’s Free Firebase Hosting service for developers. https://firebase.google.com/products/hosting/.
If this attack was hosted on a unique domain, and hosted used proper hosting, we may get the information about the attacker using appropriate methods. The only thing that attaches this attack to a person is the mobile number.
Let’s Begin.
This attack is attempted clearly by an amateur, who is most likely using only a mobile device. As you can see from the screenshot, the page title says “Wellcome”.
The original logo image is in correct dimessions, but the attacker managed to mess it up somehow.
The Captcha image is static, the refresh button only for the lulz, methinks. Or, incompetence? There is no place to enter the captcha, too.
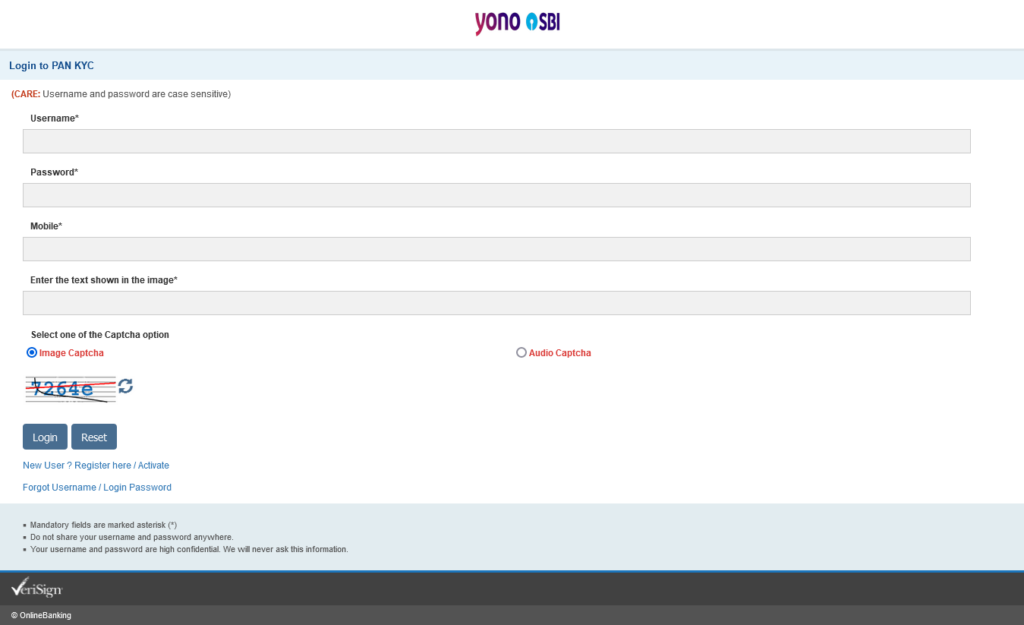
When you click the Audio Captcha, the Image Captcha stays selected too. This is actually worse, at least with image Captcha, you could see an image, here you don’t even have an audio file.
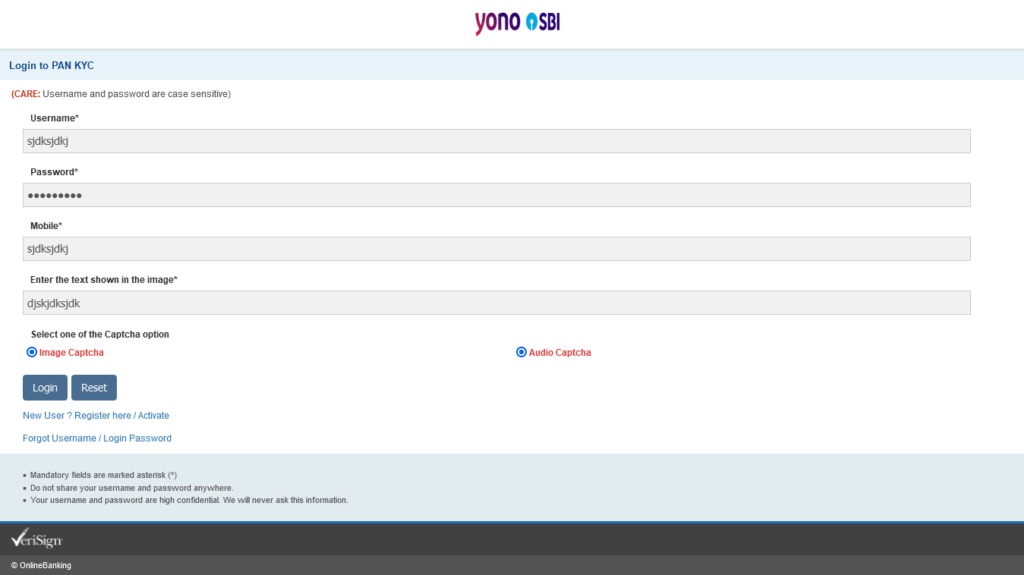
The only saving grace is the Reset button, which actually works. The login button works, too, actually.
Entering junk “Credentials” took me to page 2, I guess. https://s44-fhvb.web.app/p2. Page 2 still says “Wellcome”. At least, change it to Welcome.
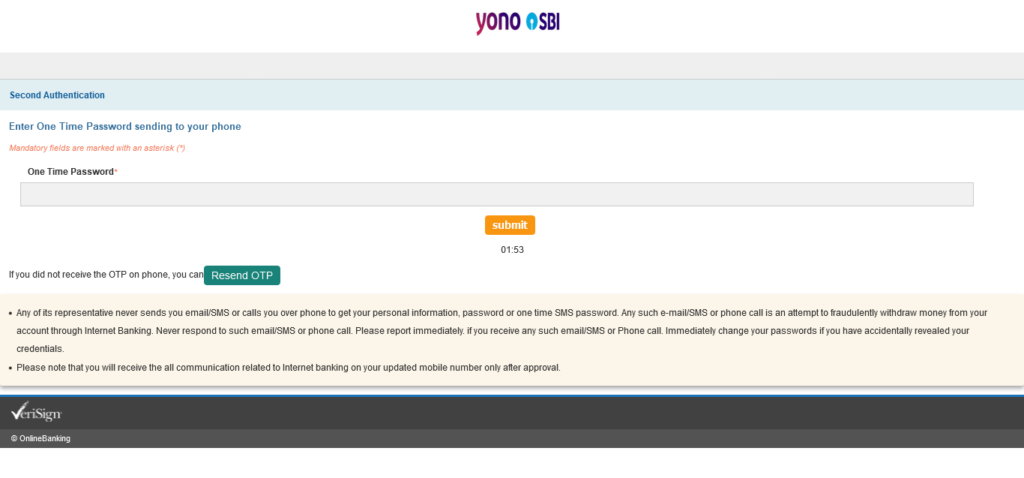
There is a 3 minute timeout. After those 3 minutes, it just stays at 00:00.
I received no OTP. Apparently, according to the attacker, SBI sends letter-based OTP as well. Brilliant!
Resend OTP button doesn’t work.
Sending fake OTP takes you to Page 3 with URL – https://s44-fhvb.web.app/p3, again titled “Wellcome”.
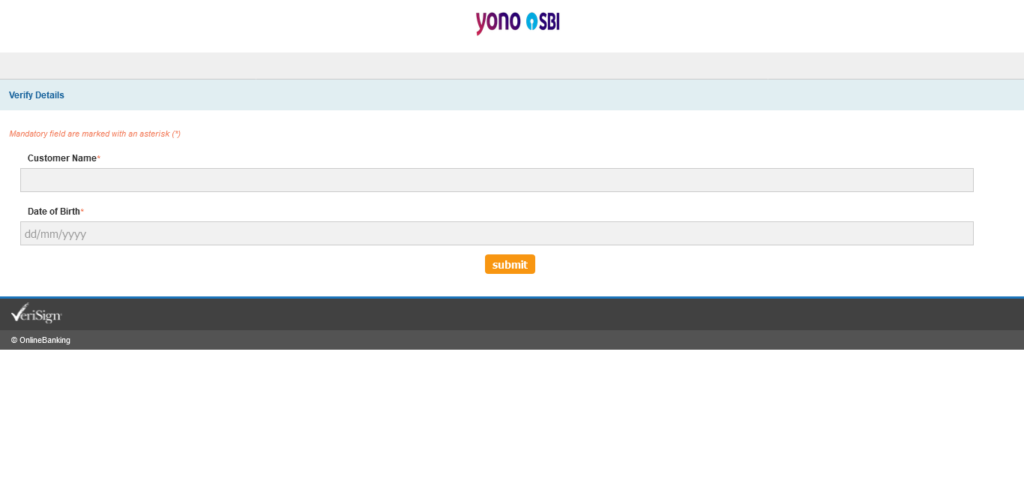
Here you see Customer Name and Date of Birth. Entering any date works. Clicking Submit takes you to page 4, and guess what it says? “Wellcome”.
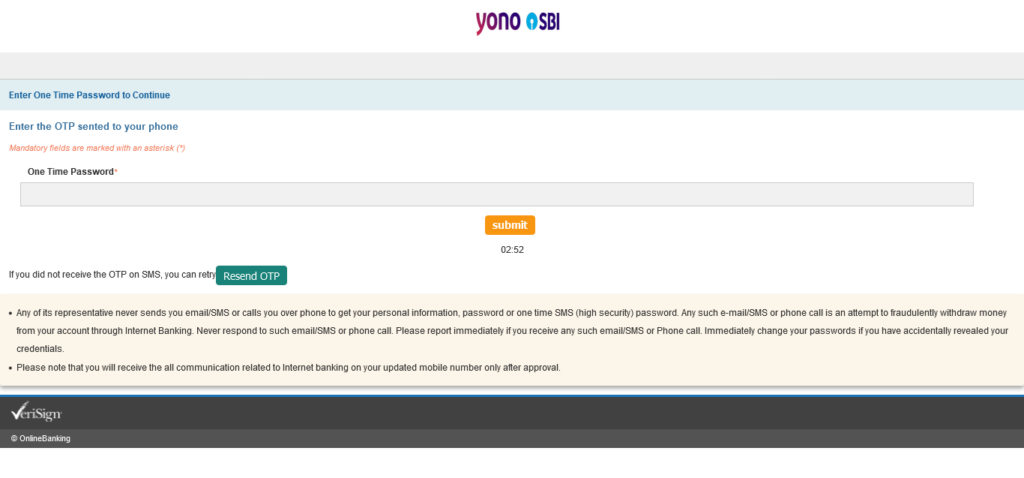
Here, we have to enter another imaginary One Time Password to make a two-time person happy.
We see a 3 minute timeout, again. After those 3 minutes, it just stays at 00:00. The Resend OTP button doesn’t work.
To my surprise, the OTP did not work this time. Same old story, Page 5, “Wellcome”.
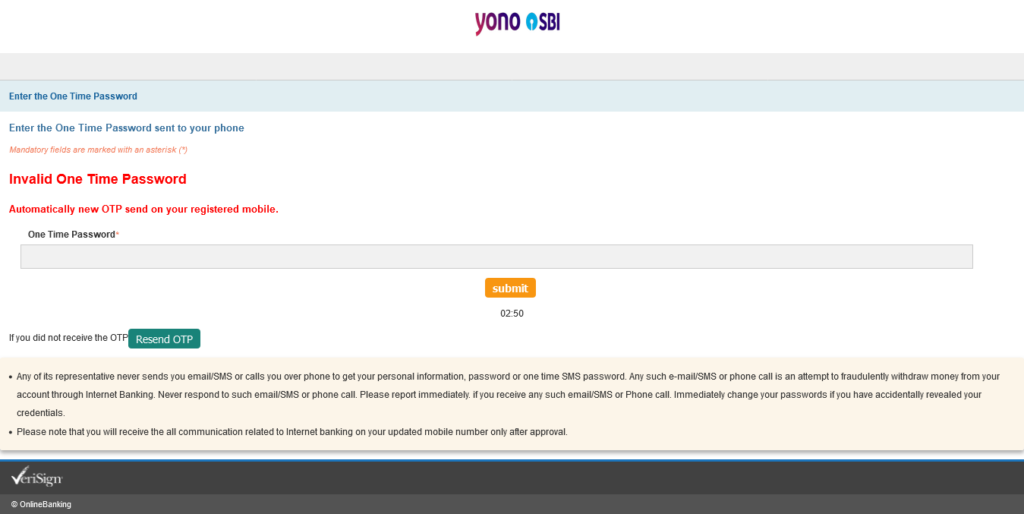
The page alerts us (in deep red):
Invalid One Time Password
Automatically new OTP send on your registered mobile.
This time, I entered all digits, it worked, we move to the next “Wellcome” page. Yes, you guessed it right, Page 6.
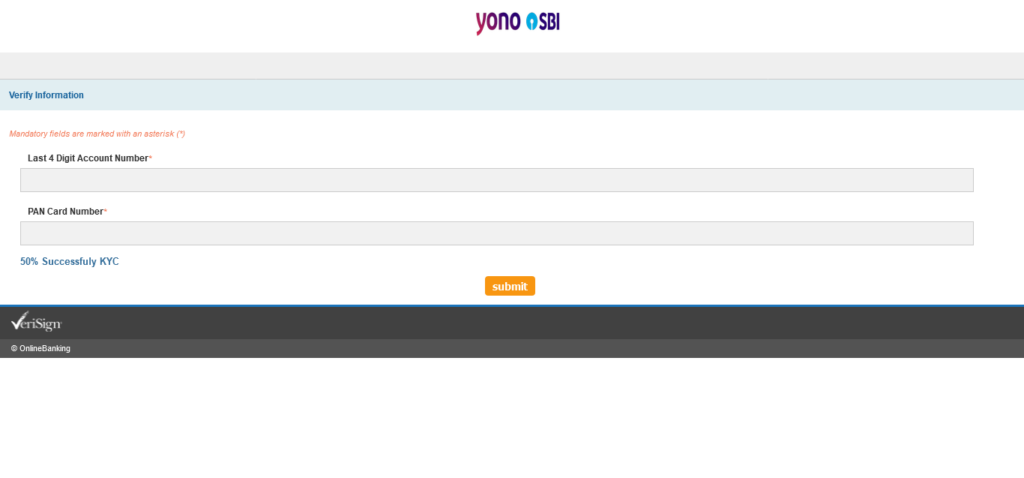
Here we see two text-input boxes – Last 4 Digit Account Number* and PAN Card Number*
I wonder why it says “50% Successfuly KYC” at the bottom. 2 things bother me, 50% and Successfuly.
No timeouts here.
I guess anything works here, too.
Nope, it asks me to enter the PAN number is correct format, so I enter XXXXX0000X.
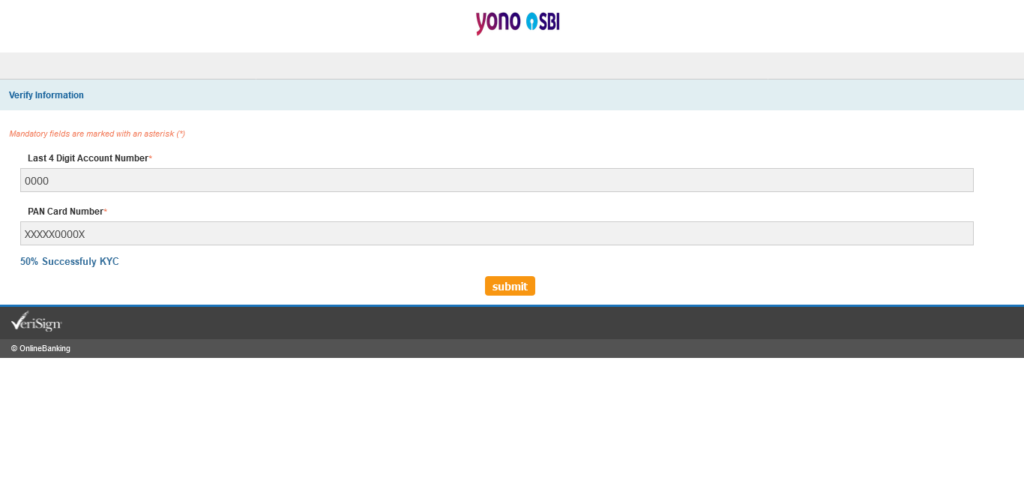
Aaaand, we are back to the OTP page (p7) titled “Wellcome”
3-minuted timeout, Reset still doesn’t work. Timeout doesn’t reset.
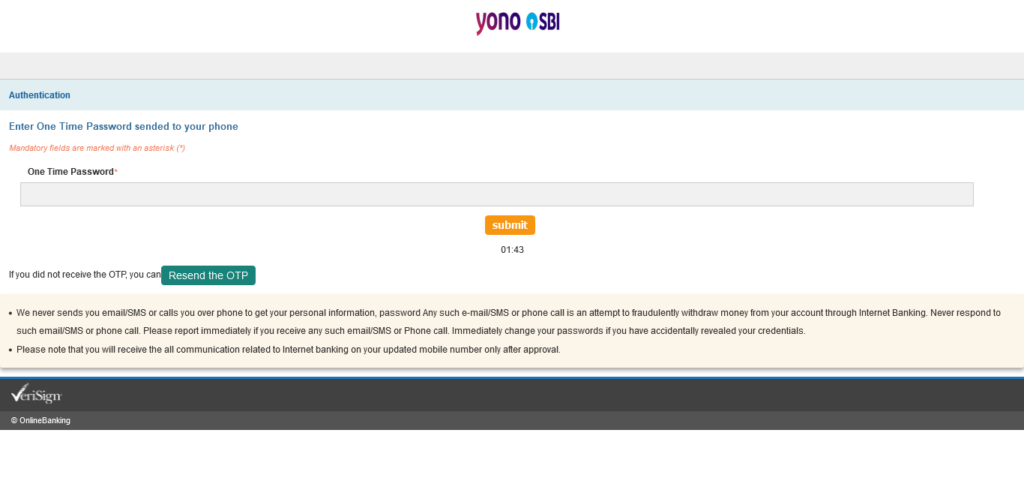
On Page 8, I enter all-letter OTP.
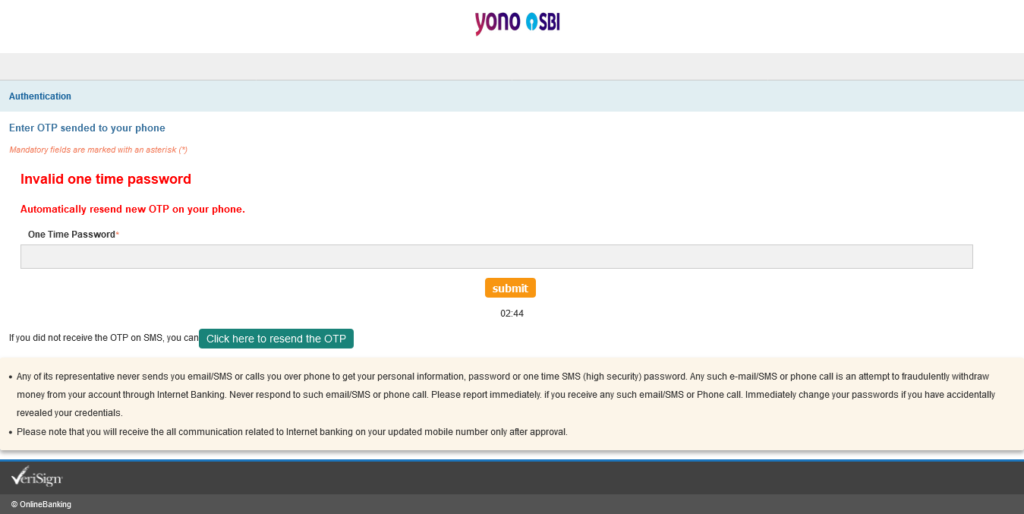
This OTP doesn’t accept all-letter OTP. Entering an all-digit OTP takes us to page 9. At first, I thought, it’s the same as Page 6, but no, This page is used to gather more information from you. Here, you find the option to submit your Aadhar (UID) number and Email address to the attacker.
Last 4 Digit Aadhar Number*
Email*
It has an 80% Successfuly KYC. Okay.
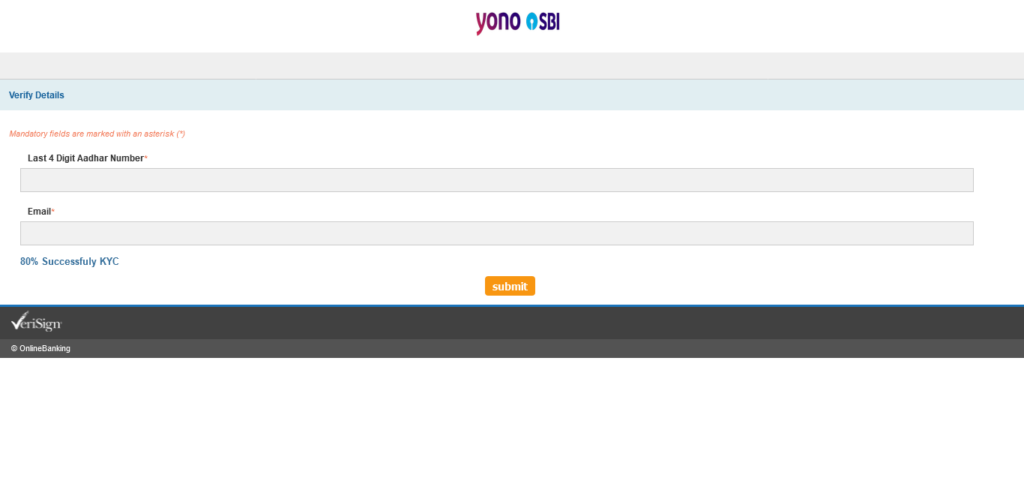
The attacker accepts an all letter-based Aadhar, but gets all crazy on me when I don’t use correct email format. To each his own.
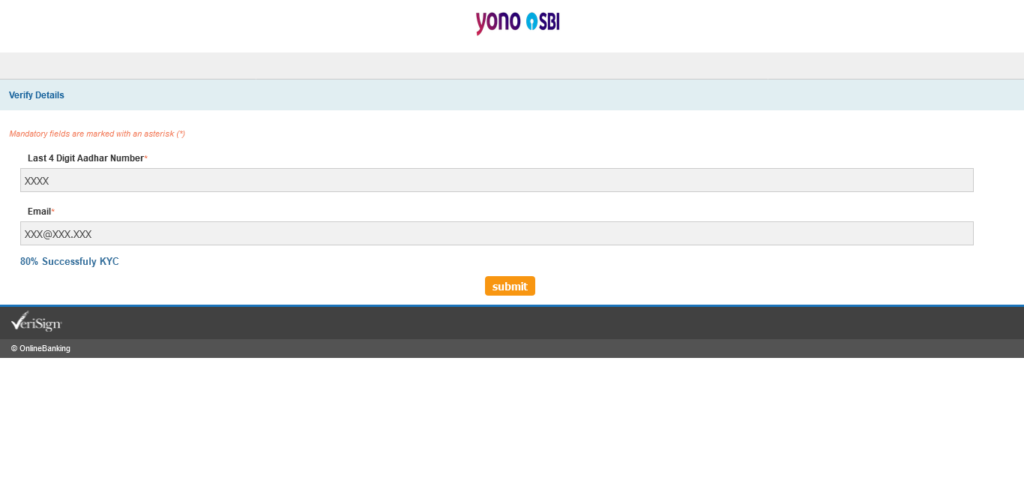
Entering a random email takes us to another OTP page (Page 10, Wellcome).
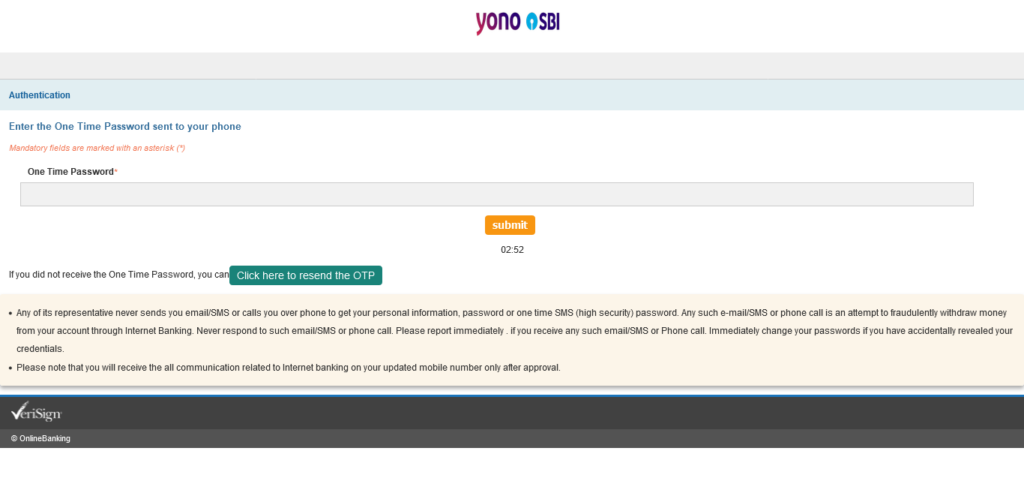
No matter what you enter here, you’ll be redirected to Page 11 where it says, “Automatically resended new One time Password on your phone.”
Entering anything takes you back to page 10. From here on onwards, it’s a loop.
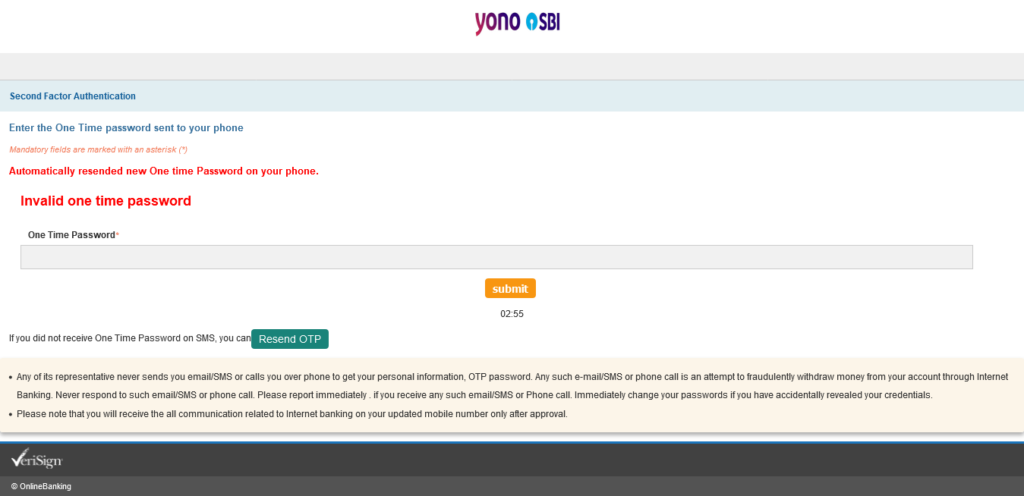
That’s it, folks. The end of the road. All the information that you entered in all these steps went to the attacker’s server, not to the SBI. This is how you become the victim of a Phishing attack.
What you can do to protect yourself from Phishing Attacks?
This has been a bad example of Phishing. But, not every phishing attempt sucks. Most of them work, so it’s important for you to take this very seriously.
- Do not click such random links sent to you in SMS messages, WhatsApp (or other messenger apps), or in your emails.
- Do not respond to these random phone numbers/emails.
- Always check the URL before entering sensitive information. Check the bank’s website address (URL). If it ends with .com, then make sure there is a forward slash (/) after that .com, and not another dot (.) followed by another string of letter (and numbers).
- Check the green lock sign.
- Check that the site is served from secure protocol – https.
- Check for grammar mistakes on these pages. Those are a easy and good giveaways.
- If there is urgently factor involved, always ask yourself, “why?”.
- Click spam of emails containing such phishing emails.
- Report such messages on WhatsApp as soon as you receive them.
- Use Block sender on your SMS app. If your service provider has an option to submit phishing, malicious numbers, please do so, too.
- Report the domain name to the domain name registrar.
- Report to the web hosting provider.
- Check these login URLs on URL testing websites. Here are a few options.
- https://www.virustotal.com/gui/home/url
- https://sitecheck.sucuri.net/
- https://urlscan.io/
- https://threatcenter.crdf.fr/check.html
- https://www.urlvoid.com/
- https://transparencyreport.google.com/safe-browsing/search
- https://urlhaus.abuse.ch/browse/
- https://www.ipvoid.com/
- https://www.spamhaus.org/lookup/
- https://www.phishtank.com/
At the time of writing this post, this (sub)domain was not marked as Phishing.
